Understanding Data Encryption and Decryption Techniques
In the OSI model, data moves in two directions: downwards, where it undergoes Encryption, and upwards, where it goes through Decryption.
When computer encapsulate data, it means the information travels through each layer of the OSI model, undergoing various transformations at each stage.
Data Encryption Process
When computer encapsulate data, it means the information travels through each layer of the OSI model, undergoing various transformations at each stage.
- User Interaction (Application Layer): The journey starts at the Application layer where the user interacts with an application. The data generated by the user is then passed to the Presentation layer and subsequently to the Session layer.
- Adding Information (Presentation and Session Layers): These layers add extra information to the original user data, preparing it for transmission and passed it to the Transport layer. In the Application, Presentation, and Session Layers, the Protocol Data Unit (PDU) is simply referred to as “Data”.
- Segmentation (Transport Layer): In the Transport Layer, the Protocol Data Unit (PDU) is named differently depending on the protocol used. When using TCP, the PDU is known as a “segment.” In the case of TCP, the data is divided into smaller pieces, and a TCP header is attached. Each of these pieces is now called a segment, and they are organized in a sequence to facilitate accurate reconstruction when received on the other end.
- Now, if we’re talking about UDP, the PDU goes by the name of a “datagram.” A datagram is a standalone unit of data that is sent independently, without establishing a connection first. It offers simplicity and low latency but lacks guaranteed delivery and ordered transmission.
- Logical Addressing and Routing (Network Layer): The segments/datagrams are handed to the Network layer, where network addressing (logical addressing) is applied, and routing through the internet network takes place. At this point, the data, including the transport header and upper layer information, becomes a packet. The Network layer adds its IP header to the packet.
- Encapsulation in Frame (Datalink Layer): The packet is then sent to the Datalink layer, which encapsulates it in a frame. This frame includes the hardware addresses (MAC) of the source and destination computers, LLC information for protocol identification, and an FCS field for error checking.
- Digital Signal (Physical Layer): To send the frame over the network, it needs to be converted into a digital signal. The Physical Layer takes care of this by encapsulating the logical group of 1’s and 0’s into a digital signal that other devices on the local network can interpret. Additionally, a few extra 1’s and 0’s are added at the beginning of the frame. This is done to help the receiving end synchronize with the incoming digital signal, ensuring proper interpretation of the data. Think of it as a kind of prelude to the actual frame, allowing the receiving device to tune in correctly to the upcoming information.
This process ensures that data is properly prepared, segmented, addressed, and encapsulated at each layer, making it ready for reliable transmission across a network.
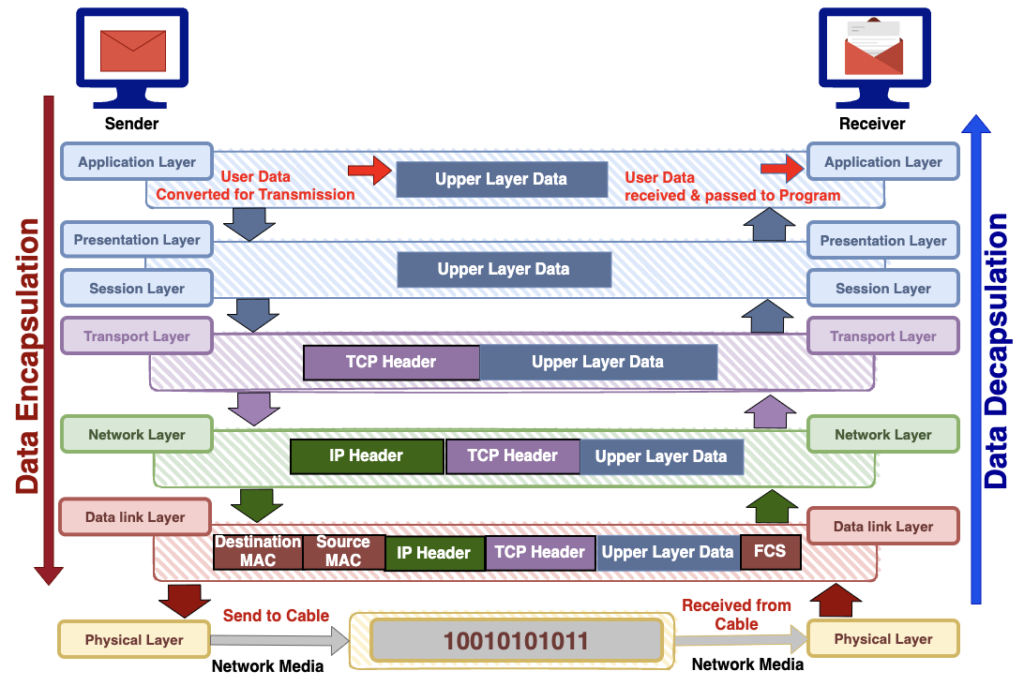
Data Decryption Process
When the destination computer receives the data:
- Synchronization (Physical Layer): Upon receiving, the computer initially synchronizes with the digital signal by interpreting the additional 1’s and 0’s mentioned earlier. Once synchronization is achieved and the entire frame is received, it then forwards the frame to the layer directly above it, which is the Datalink layer.
- Datalink Layer Processing: The Datalink layer performs a Cyclic Redundancy Check (CRC) on the frame for error checking. If the result matches the value in the Frame Check Sequence (FCS) field, it assumes the frame is error-free. The Datalink layer then removes any information added by the sender’s Datalink layer and passes the rest (now called a packet) to the Network layer.
- Network Layer Processing: At the Network layer, the IP address is checked. If it matches the computer’s own IP address, the Network layer header (or IP header) is stripped off from the packet. The remaining data is then passed to the Transport layer.
- Transport Layer Processing: Here, the remaining data, now called a segment, is processed. The Transport layer rebuilds the data stream, acknowledging to the sender for each received piece. The use of an acknowledgment (ACK) indicates the use of TCP rather than UDP. After this, the data stream is handed over to the upper-layer application.
In analyzing data transfer between computers, many focus on layers 1 to 4 (Physical to Transport) or at most layer 5 (Session), depending on the type of data being transferred. The detailed examination often doesn’t go beyond the Transport layer.



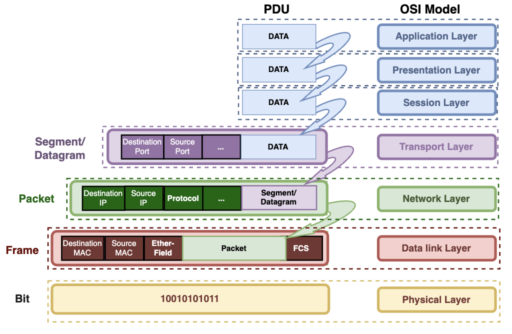
For me it is quite informative and well-structured. Expecting that you will describe TCP/IP packet format in detail
I appreciate your feedback and interest in understanding the TCP/IP packet format. I will try to make it within the shortest possible time.